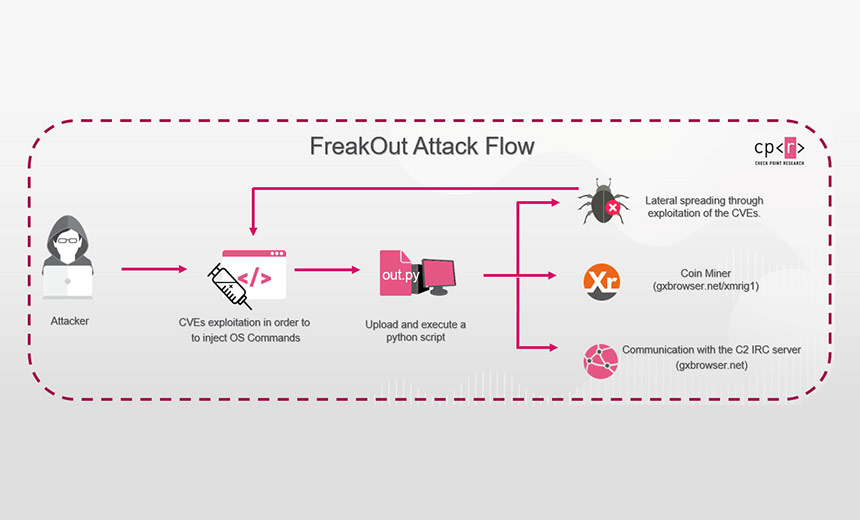
PDF) An Aggregated Mutual Information Based Feature Selection with Machine Learning Methods for Enhancing IoT Botnet Attack Detection
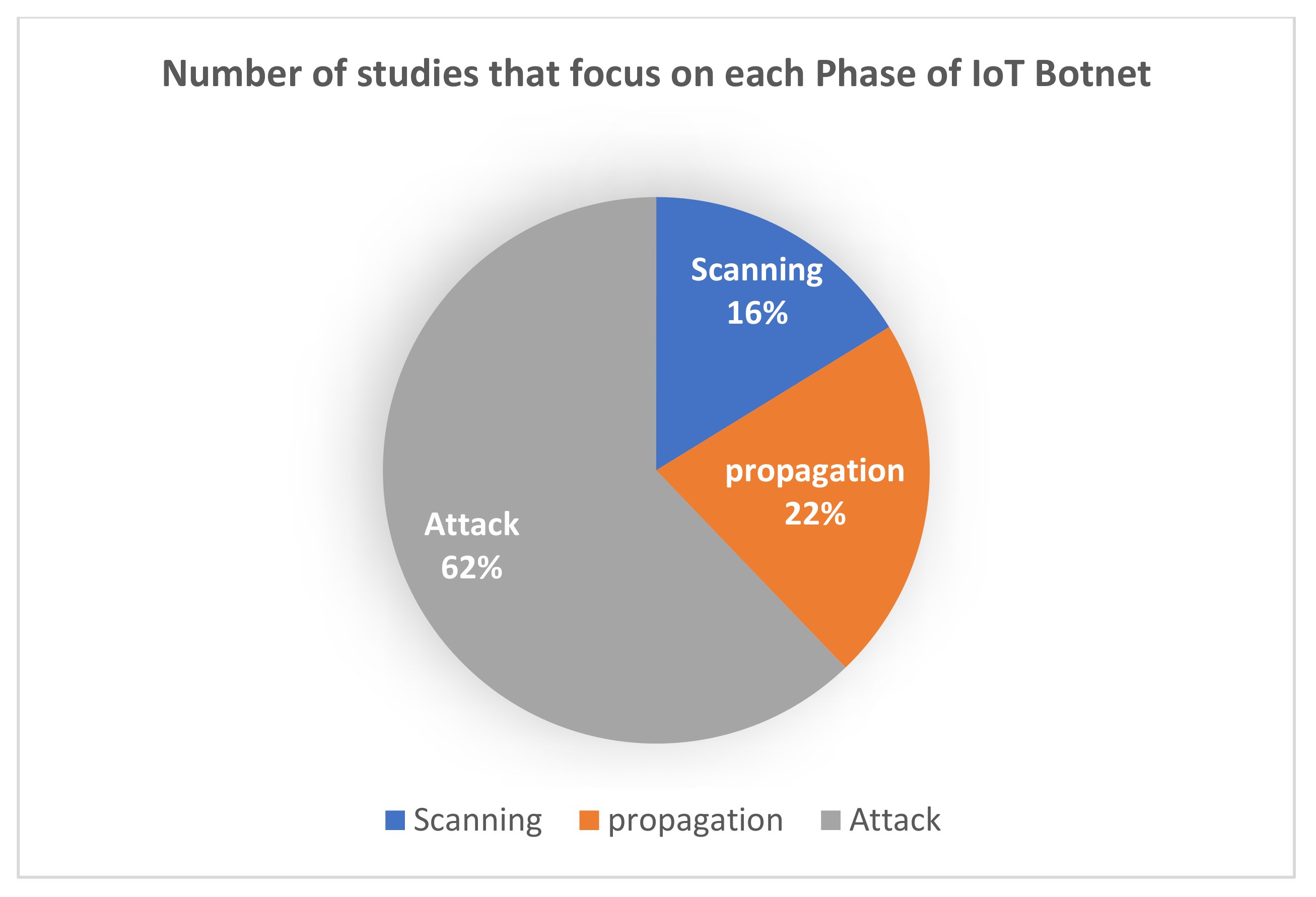
Applied Sciences | Free Full-Text | Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research | HTML

Applied Sciences | Free Full-Text | Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research | HTML